CzechIdM 7 – product description
CzechIdM 7 is the latest generation of the identity manager, which administers over 3 million user accounts in not only Czech companies. Our experience from managing identities of our existing customers has been used during its development. This version is the answer to requests of users, administrators, and developers.
Check out our online demo at http://demo.czechidm.com/ and see our precious.
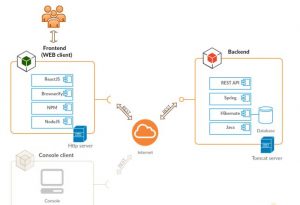
CzechIdM 7 is an application divided into a backend and a frontend part.
The backend part is written in Java using the Spring framework. It uses a relational database to store data. It communicates with the outside world (including frontend) primarily through the REST interface and standardized connectors.
The frontend part is written in JavaScript using ReactJS and NodeJS.
CzechIdM supports running on multiple application servers at the same time to provide load balancing or high service availability.
1.1 CzechIdM configuration options
The administrator can set the entire environment of CzechIdM without the need for development, by configuring the following parts:
- Configuration of connected systems.
- Synchronize identities from one or more sources, such as a personal system and a database of external contractors.
- Create roles (manually and synchronize from source, e.g. MS AD)
- Set rules for automatically assigned roles
- Set policies for passwords, notifications, and other parts of the system.
- Throughout the identity manager, work with more than one contracted position is supported natively – the roles are thus assigned to a particular contracted position. If the contracted position expires, role is automatically removed from the identity.
- Out of the box, CzechIdM contains configurable standard automatic identity processes:
- Enabled contract
- End of contract
- Work position change
- Contract exclusion (maternity / parental leave)
Multiple contracted positions
1.2 Integration with the other systems
It is possible to connect any system available to the CzechIdM via the network and the known structure of the objects (identities, roles …). CzechIdM allows you to manage user accounts, permissions, organizational structure on remote systems through appropriate connectors. It is a communication interface that uses the native API of the connected system to communicate with the managed system. When connecting systems to CzechIdM, there is no need to modify the interfaces of the remote systems.
If we do not have a specific connector for the system, we will use a generic connector (such as scripting) or we will develop it.
1.2.1 Most frequently connected systems
Public Administration and Local Government – Agendas and Records Services:
- Gordic Ginis
- ICZ eSpis
- ICTBrains Matrix
- BBM iFIS – finanční řízení
- Vera
Domain Controllers and Directory Services:
- Microsoft Active Directory
- Kerberos
- LDAP/OpenLDAP/Free IPA
- Novell eDirectory
Mail services:
- MS Exchange
- Office 365
- Linux postfix
- CommuniGate
- Zimbra
General connectors:
- Database connector
- JDBC scripted connector (fore more complex databases)
- SSH scripted connector (linux servers)
- SCIM connectors
Databases:
- Microsoft SQL Server
- MySQL
- Oracle
- PostgreSQL
- Progres
Operating systems:
- HP-UX
- Linux distributions without restrictions – Red Hat, Debian, SuSE,…
- Microsoft Windows all versions
- Solaris
- S/400
HR systems:
- VEMA
- OKbase
- HRIS
- Mysys HRMS
- Target
- Navision
- SAP
- Helios Green
Service Desks:
- HPSM
- Siebel
- Conclusion
- Request Tracker
Health-care systems:
- StaproMEDEA NIS
- StaproPANAKEA
- OpenLIMS
- LEKIS
- AMIS – H
1.3 Role management
In its GUI, CzechIdM offers the ability to request roles that assign permissions to managed systems or to identity manager.
Interesting features of roles:
- Role guarantors (owners)
- Various approval workflows for roles
- Role assignment from-to
- Criticality of roles
- Merge roles
- Automatically assigned roles according to the organizational structure
- Synchronize roles from an external source
- Export roles to a managed system
- Cataloging roles
Basic role configuration
List of role’s users
1.4 Notification
CzechIdM allows you to define different channels for event notification – for example, Email. Events in CzechIdM are represented by so called Topics. Administrator has the ability to configure which notification channel will be used for which topic. For example, for „Sending Reset Passwords“, use the option to send via SMS.
Interesting features of notifications:
- Templates for notifications
- Email, SMS and Web application interface
- Configuring the notification method by the administrator for each type of notification, such as: a new password by SMS, but information about approving the change of rights by email
Overview of emails sent from CzechIdM
Configure the mail template in the GUI
1.5 Authentication
The unified authentication system is modular to the extent that it allows you to configure different ways (local password, authentication against a managed system – such as LDAP, OpenAM, SSO integration) or adding custom authentication.
1.6 Division into separately managed areas
CzechIdM allows you to divide a single instance into a separate region/parts (REALM), which allows the separation of separate self-running organizations in one identity manager. Administrators and users from individual areas do not have the ability to interfere with other areas. But they can share „globally“ available resources, such as linking to MS Active Directory, etc. There is still a single supervisor’s identity manager environment available on separate areas, which allows centrally managing both identities and their permissions, and the application itself.
This division facilitates the introduction of identity management in the holdings environment and various business groups that have shared IT but separate and often competing organizations.
1.7 Time machine
An important part of identity management is to prove past changes made to identities and their permissions. CzechIdM introduces the so-called Time Machine. Each time an object is changed (identity, role, managed system …), a snapshot is created. Whenever you can browse and compare revisions between any two snapshots and the current status.
1.8 Confidential storage – Vault
An secure encrypted storage is available for sensitive information stored in IdM. An attribute labeled „secret“ is immediately stored in a confidential storage after it has been received from the synchronization or web interface and is only picked up when it is needed. For example, when writing to a managed system. Secure storage also stores credentials for managed systems.
Data in confidential storage is encrypted and is stored in the IdM database by default. In case of a higher security requirement, you can use a Vault storage that requires multiple people to participate in the decryption process. Without encryption, Vault will not allow IdM to run.
A secret attribute in the configuration of a managed system
1.9 Easily update and enhance functionality
The application uses modules that enable easy expansion of CzechIdM functionality or customize application behavior to the customer’s environment without having to intervene in the product.
Sample of available modules:
- Self-registration of users
- Integration with a certificate authority
- Manage VPN accesses
- Integration with SMS gateway
2 Brief summary of product properties
| Brief summary of product properties | ||
| General application features |
|
|
| Identity |
|
|
| Account management |
|
|
| Contracted positions |
|
|
| Organizational structure |
|
|
| Roles |
|
| Supported connectors |
|
| Synchronization |
|
| Authorization of data access |
|
| Notifications |
|
| Audit |
|
| Modularity | Modules expanding functionality:
|