CzechIdM manages MS AD cross domain groups
In MS Active Directory, groups can have members not only from the same domain but also from other trusted domains. This is determined by „type“ of a group. Such cross domain group membership can be now managed by CzechIdM.
Supported types of groups
MS ActiveDirectory (AD) and Exchange identity connectors in CzechIdM can manage membership in many types of groups. Major types are:
| Group type | groupType value | Supported |
|---|---|---|
| BuiltIn Group | -2147483643 | YES |
| Global Security Group | -2147483646 | YES |
| Local Security Group | -2147483644 | YES |
| Universal Security Group | -2147483640 | YES |
| Universal Distribution Group | 8 | YES |
| Local Distribution Group | 4 | YES |
| Global Distribution Group | 2 | YES |
Type of a group and its features are defined by the groupType attribute. The value consists of a mixture of hex flags, each activating or deactivating a specific feature. However, via LDAPv3 interface the value is represented as an Integer number. To allow members from other trusted domains, you must first configure the group in AD as “Local Group” (e. g. „Local Security Group“ or „Local Distribution Group“) which can be done by MS Active Directory Administration Interface or via setting the specific value (4 for distribution groups or -2147483644 for security groups) to the attribute.
Manage cross domain membership
We have enhanced the MS Active Directory identity connector to support cross-domain membership of managed users and contacts. The only configuration to do in CzechIdM is to assign a role which adds group’s distinguishedName as a value to the “member” attribute to the user.
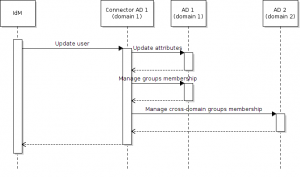
Each connector for each domain uses its own system administrator account. Suppose you want to add user into a group in other domain. The administrator account of the user’s „home“ domain needs to be granted with same administrator permissions also in the „target“ (where the group exists) domain. That’s because CzechIdM and the Active Directory connector manage group membership of the user by setting account’s “member” attribute and provisioning the user account, not by updating and provisioning the cross-domain group. So the connector in domain where the user account comes from performs the whole operation including the part on the other domain controller. The process is shown in the picture.
For CzechIdM to support the whole life-cycle management of “Local” groups, you have to configure group roles which fill attribute groupType with a certain value. To load “Local” groups into CzechIdM (e. g. via Reconciliation or Synchronization of a resource) you need to implement a rule which resolves the “Foreign security identifier“ of a group members from foreign trusted domains to identifiers (e. g. GUID) of the certain user accounts managed by CzechIdM.
Yes, CzechIdM can
Thanks to the improvement of the Active Directory connector, CzechIdM can manage cross-domain membership in MS Active Directory groups and also the whole life-cycle of many types of groups, including the “Local Security” and „Local Distribution“ groups.
If you have any questions, either about Active Directory, Identity connectors or CzechIdM, please send us email to info@bcvsolutions.eu.