Managing MS Active Directory and Exchange 2010 by CzechIdM
Recently, we connected systems MS Active Directory and MS Exchange 2010 to our Identity Manager CzechIdM for one of our customers. User accounts in the AD domain and their mailboxes would be managed automatically, which would save the time of administrators of these systems and ensure that the data would be always up-to-date with the personal system. Our customer had also some specific requirements, the solution of which you will find in this article.
Connection to CzechIdM
We used connectors developed by the project OpenICF to connect MS Active Directory (AD) and MS Exchange. Vojta Matocha already described the principle of Exchange Connector and its installation process in his article. As we mentioned at the beginning, this article will cover the solution of several specific requirements in the accounts management, which sometimes required also customization of the Exchange Connector.
Managing child domains
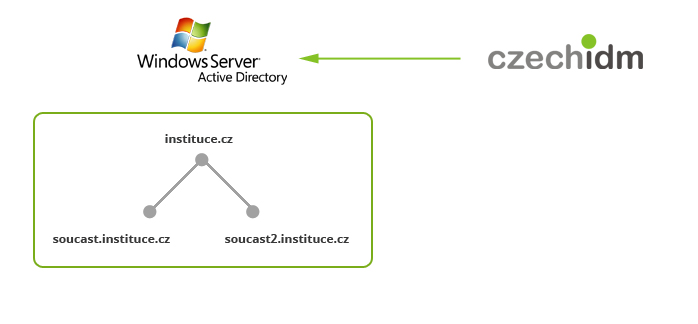
Our customer is a big institution, under which several separate parts belong. The employees of the main institution have accounts in the parent domain, we will call it e.g. instituce.cz. Every separate part uses own child domain, e.g. soucast.instituce.cz. The default configuration of the Exchange connector is not prepared for managing domain forest. What do you have to do to manage accounts in child domains?
- The connector adds to every PowerShell command it calls also the parameter
DomainController, the value of which is taken from the configuration of the connected resource (namely Active Directory Domain Controller Hostname). But the parameterDomainControllerhas to be filled in by the hostname of the domain controller of the domain in which we want to take the action, i.e. dc.soucast.instituce.cz. Therefore, we added the attributeDomainControllerto the configuration of the connected resource in CzechIdM, and the value of the attribute is filled by the rule, which dynamically finds out, in which (child) domain should the user account belong. - The administrator’s account, which CzechIdM uses to log into AD, has to belong to the group Enterprise Admins (in the domain instituce.cz) and Domain Admins (in soucast.instituce.cz). Otherwise, you get general error messages like „The server is unwilling to process the request“ or „No provisioning handler is installed“.
- The scheme of the child domain must be prepared for Exchange. This is usually done by the AD administrator during the installation of Exchange, but test environments sometimes differ (which was our case). Then you would see the message „Could not find any available Domain Controller in domain DC=soucast,DC=instituce,DC=cz“
When managing AD accounts you have to remember that accounts can’t be directly moved from one domain to another (child) domain. To enable this feature, you would have to install special tools called Active Directory Migration Tools. When attempting to change the domain of an account without these tools installed, you get the exception „DirectoryServicesCOMException: A device attached to the system is not functioning“. Our customer doesn’t need to migrate accounts between domains, so this article will not cover AGMT.
Mailbox databases
If we need email accounts for many users, it’s worth it to create more mailbox databases, across which we can distribute the workload. For example, mailboxes can be distributed across two databases according to the alphabetical order of users‘ surnames. However, people sometimes change their surnames, especially women do, so we need to know how to move mailboxes between databases.
In MS Exchange, moving a mailbox requires so called „move-request“ created with the command New-MoveRequest. Exchange then performs the move in a few minutes. Afterwards, if you needed to move a mailbox again, you would have to remove the previous move-request first, using the command Remove-MoveRequest. The whole operation in PowerShell looks like this:
Remove-MoveRequest -Identity 'test@instituce.cz' // Removing old move-request
New-MoveRequest -Identity 'test@instituce.cz' -TargetDatabase DB_A_K // Creating new move-request
Get-MoveRequestStatistics -Identity 'test@instituce.cz' // Checking the status of the move-requestWe added this functionality into the Exchange Connector, because its current version doesn’t support moving mailboxes. We extended the connector by the first two PowerShell commands, where in the Remove-MoveRequest command we added the parameter Confirm=false in order to disable the interactivity of the command. Then we added the attribute TargetDatabase to the configuration of the connected resource in CzechIdM. This attribute is always filled in by the same value as the attribute Database. Finally, we set the attribute homeMDB (the DN of the mailbox database) as read-only, so CzechIdM wouldn’t change its value explicitly.
Email aliases
Every email account in Exchange has one primary email address and an arbitrary number of other email aliases. The addresses are filled in by the attributes ExternalEmailAddress and proxyAddresses in the configuration of the resource in CzechIdM; you won’t make a mistake if you fill in both these attributes. The correct value for these attributes is a list of email addresses with prefix „SMTP:“ (primary address) or „smtp:“ (other aliases). Primary email address is also set by the attribute PrimarySmtpAddress and in this attribute, on the contrary, we don’t use any prefix.
Thumbnail photo
A thumbnail photo is an image, which AD saves in the attribute thumbnailPhoto as an array of bytes. This image is used by other applications that are integrated with AD, e.g. in Exchange, you can see the image in the profile info of the user who sent you an email.
We extended the AD Connector (submodule of the Exchange Connector) in the following manner: CzechIdM sends a path to the photo file in the attribute thumbnailPhoto, the connector retrieves the given file and saves its bytes to AD attribute thumbnailPhoto. To achieve this, the class CustomAttributeHandler has to be extended by a new handler for the attribute thumbnailPhoto.
Security groups for the administrator’s account
Little recapitulation of necessary administrator’s account’s privileges definitely won’t hurt anybody. This account needs to create accounts in AD and mailboxes in Exchange, both on all parts of the domain forest. We had to spend some time with the configuration of AD to get the necessary set of security groups and probably we weren’t neither the first nor the last one trying to achieve this. Now we know that everything works correctly if the administrator’s account is a member of these groups:
- instituce.cz:
Discovery Management, Domain Admins, Domain Users, Exchange Organization Administrators, Exchange Public Folder Adiministrators, Exchange Recipient Administrators, Exchange View-Only Administrators, Group Policy Creator Owners, Schema Admins, Enterprise Admins - soucast.instituce.cz:
Domain Admins
Conclusion
This article described several details of connecting MS Active Directory and Exchange 2010 to CzechIdM. If you are interested in this topic or if you consider automatic management of Active Directory or Exchange accounts in your company, don’t hesitate to contact me at alena.peterova@bcvsolutions.eu.